What is OpenID Connect Authentication and Benefits of Using OpenID Connect?
What is OpenID Connect Authentication and Benefits of Using OpenID Connect?
Introduction
OpenID Connect has revolutionized the authentication process and quickly made its way to the top in a very short span of time. It is mainly used in the single sign-on and identity provision on the Web. The main reason for its success is its Simple JSON-based ID tokens (JWT) delivered via the OAuth 2.0 process flow which is already designed for all the internet using devices like browsers and mobile devices.


The Era before OpenId Connect?
Before the OpenID, we have used Local user Authentication for identifying the users in which we create a local database for the users’ accounts and credentials. This process is very simple and convenient for personal use, However, local authentication can be bad for business:
- People find the sign-up and account creation tedious, and rightly so. Consumer web sites and apps may suffer abandoned shopping carts because of that, which means loss of business and sales.
- For enterprises with many apps, the maintenance of separate user databases can easily become an administrative and security nightmare. You may want to put your IT resources to better use.
The established solution to these problems is to delegate user authentication and provisioning to a dedicated, purpose-built service, called an Identity Provider (IdP).
Google, Facebook, and Twitter, where many people on the internet are registered, offer such IdP services for their users. A consumer web site can greatly streamline user onboarding by integrating login with these IdPs.

Entry Of OpenId Connect
OpenID Connect, published in 2014, is not the first standard for IdP, but definitely the best in terms of usability and simplicity, having learned the lessons from past efforts such as SAML and OpenID 1.0 and 2.0.
What is the formula for the success of OpenID Connect?
- Easy to consume identity tokens: Clients receive the user’s identity encoded in a secure JSON Web Token (JWT), called an ID token. JWTs are appreciated for their elegance and portability, and for their ready support for a wide range of signature and encryption algorithms. All that makes JWT outstanding for the ID token job.
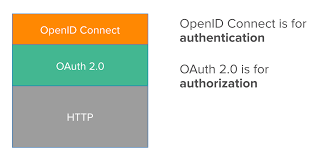
- Based on the OAuth 2.0 protocol: The ID token is obtained via a standard OAuth 2.0 flow, with support for web applications as well as native/mobile apps. OAuth 2.0 also means having one protocol for authentication and authorization (obtaining access tokens).
- Simplicity: OpenID Connect is simple enough to integrate with basic apps, but it also has the features and security options to match demanding enterprise requirements.

The Work-flow
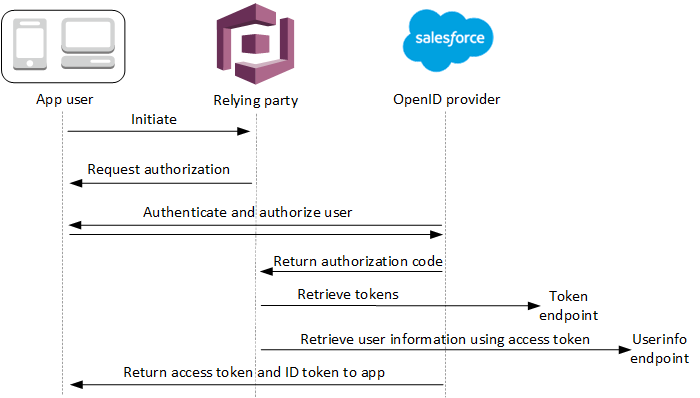

When your user signs in to your application using an OIDC IdP, this is the authentication flow
- Your user starts with the Amazon Cognito built-in sign-in page and is given the option to sign in through an OIDC IdP such as Salesforce. Here the OIDC IdP mechanism is being provided by the salesforce.
- Your user is redirected to the OIDC IdP’s authorization endpoint provided by the salesforce.
- When your user is authenticated by the salesforce, the OIDC IdP redirects to Amazon Cognito with an authorization code.
- Amazon Cognito exchanges the authorization code with the OIDC IdP for an access token.
- Amazon Cognito creates or updates the user account in your user pool for that user.
- Amazon Cognito lends your application bearer tokens, which can include identity, access, and refresh tokens.
Benefits of Using OpenID Connect
The major factor of using OpenID Connect is that it provides a complete standardized setup, with no additional worries. Since it is built on the top of OAuth 2.0 it is API ready, but adds the extra information with OAuth so that the client can know who logged in, how strongly, etc.
OpenID Connect never defines how authentication is done but it provides a standardized law on how to ask for it, and how the result of authentication should be displayed for the client.
The response -request format of the OpenID connect is in JSON which is human-readable as well as it works really well for the data-interchange operations.
OpenID Connect is a protocol designed in such a way that it equally supports mobile applications with web applications. It works well in both mobile apps and web apps. It synchronized itself greatly with the Single Sign-On (SSO).


