Cloud Audit logs in GCP
Cloud Audit logs in GCP
11 June 2021
Introduction
Google Cloud Platform (GCP) is a set-up of distributed computing administrations for sending, overseeing, and checking applications. A basic piece of conveying solid applications is making sure about foundation. Google Cloud Audit Logs records who, where, and when for action inside the current circumstance, giving a breadcrumb trail that managers can use to screen get to and distinguish expected dangers across the assets (e.g., capacity basins, information bases, administration accounts, virtual machines). GCP gathers audit logs from all GCP services, so we can get more settings around client and administration account action for security investigation and distinguish potential weaknesses that we should address before they become greater issues.
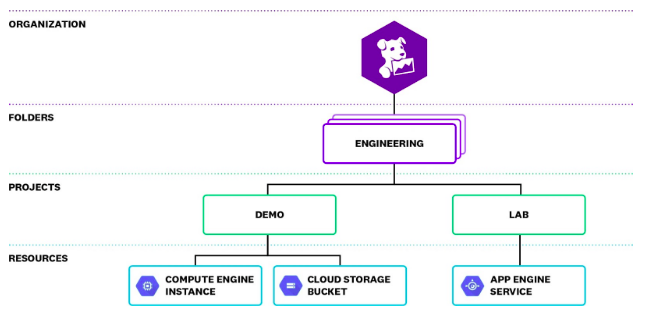
First, let’s have a look at the hierarchy of GCP
An asset chain of importance arranges the Google Cloud assets by association, task, and envelope and characterizes which individuals approach what assets. This chain of importance frequently imitates the structure of an organization, where certain assets, for example, a Google Compute Engine (GCE) case or Google Cloud Storage (GCS) can for instance, be possessed by a particular office inside the organization.
To give admittance to the assets, we can make Cloud IAM strategies. An approach can incorporate individuals from a few distinctive record types, including Google records and administration accounts. These arrangements proliferate down the pecking order. In the model above, on the off chance that we award a Google bunch the supervisor function for the Engineering organizer, their Google account certifications will consequently give them peruse and compose admittance to all the assets in both the Demo and Lab ventures. Understanding the progressive system of the association, just as the functions of individual clients and administrations, will assist us with filtering this information in the audit logs and pinpoint any expected dangers to the applications.
Understanding Google Cloud Audit Logs:
Google Cloud can produce three distinct kinds of audit logs for each association, envelope, and task inside the asset progressive system:
- Admin Activity: passages for API calls or client managerial action that changes asset designs
- System Event: sections for Google framework managerial action that alters asset setups
- Data Access: passages for API calls that read asset designs or metadata, or client level API calls that peruse or compose asset information
Most Google Cloud administrations radiate every one of these audit log types, empowering us to see asset movement for various degrees of the progressive system. This incorporates G Suite in the event that we are imparting that information to Cloud Logging, so we can likewise see the Admin Activity and Data Access audit logs that G Suite composes at the authoritative level.
We can get to the logs utilizing GCP reassurance. In the wake of signing in, select Logging from Log Viewer in the navigation menu.
Audit logs to monitor:
Cloud IAM arrangements are mind boggling and can give clients and administration accounts admittance to assets at each degree of the current circumstance’s pecking order. Observing audit logs gives a superior comprehension of who is getting to an asset, how they are getting along it, and whether the entrance was allowed.
Some normal situations that lead to the GCP account being undermined include:
- freely open GCP assets, for example, stockpiling containers or process occurrences
- misconfigured IAM consents
- misused GCP certifications
Assailants frequently search for these sorts of weaknesses to access the current circumstance. When they approach, they can alter GCP administrations, heighten advantages and make new records, and exfiltrate touchy information.
To act as an illustration of misconfigured consents, a Cloud Storage IAM strategy for the capacity cans can incorporate the worth allAuthenticatedUsers as an individual from the job Storage Object Admin. This would give all confirmed clients to GCP—not simply validated clients inside record the capacity to make, erase, and read all items inside the capacity can.
GCP gives security rules that are planned to structures, for example, CIS Benchmarks, which offer gauge best practices for making sure about the current circumstance. The audit logs supplement these rules and give an itemized history of movement, guaranteeing that we can alleviate expected dangers to the current circumstance.
Export the audit logs:
As a component of its Operations Suite (in the past Stackdriver), GCP gives Cloud Logging to questioning and breaking down the entirety of the logs. Cloud Logging utilizes sinks for sending out logs to another source. All sinks incorporate a fair objective and a logs question. We can utilize Cloud Logging sinks to trade the logs to an objective, for example, distributed storage, a BigQuery dataset, or a Publish Subscribe (Pub/Sub) subject. Cloud Logging looks at a sink’s inquiry against approaching logs and advances coordinating passages to the suitable objective.
Pub/Subs give quick, offbeat informing for the applications, and are prescribed for sending out audit logs to an outer checking administration like Datadog for additional investigation. At the point when we add a Pub/Sub theme as a sink’s fare objective, Cloud Logging will send coordinated logs to that subject. Pub/Sub points are message lines that different administrations can buy into with a Pub/Sub membership to consequently get those messages.
With the capacity to send out audit logs, we can without much of a stretch fuse them into the current checking apparatuses and get further experiences into likely security or consistency issues inside the surroundings.
Begin checking the Cloud Audit Logs:
In this blog, we looked at GCP audit logs and how they can give priceless understanding into action in the current circumstance so we can rapidly distinguish conceivable misconfigurations and dangers.