Concept of Service accounts on GCP
Concept of Service accounts on GCP
11 August 2020
Overview
A GCP service account is a type of Google account proposed to interact with non-human users that requires authentication to be confirmed in order to fetch information over Google APIs.
Usually, service accounts are utilized in situations, for example:
- Running workloads on virtual machines (VMs).
- Running workloads at on-premises workstations or data servers that call Google APIs.
- Running workloads which are not attached to the lifecycle of a human client.
Contrasts between a service account and a user account:
- Service accounts vary from user accounts in a couple of key ways:
- Service accounts don’t have passwords, and can’t sign in by means of programs or treats.
- Service accounts are related with private/open RSA key-matches that are utilized for confirmation to Google.
Cloud IAM consents can be conceded to permit different clients (or other assistance accounts) to mimic a service account.
Service accounts are not individuals from your G Suite space, not at all like user accounts. For instance, in the event that you share resources with all individuals in your G Suite space, then they won’t be imparted to service accounts. Similarly, any advantages made by a service account can’t be inherited or managed by G Suite administrators
When you conclude that you need a Service account, you can ask yourself the accompanying inquiries to see how you’re going to utilize the Service account:
- What assets can the Service account get to?
- What access does the Service account need?
How to create a service account in the GCP console?
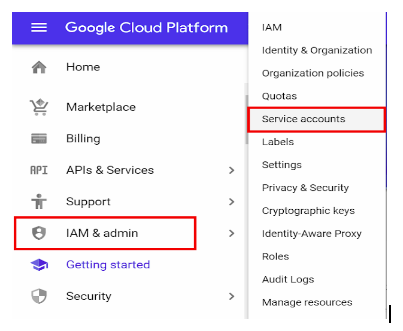
- Log in to your GCP console and click on the hamburger icon at the top left corner.
- Hover on IAM & Admin > click on Service Accounts.
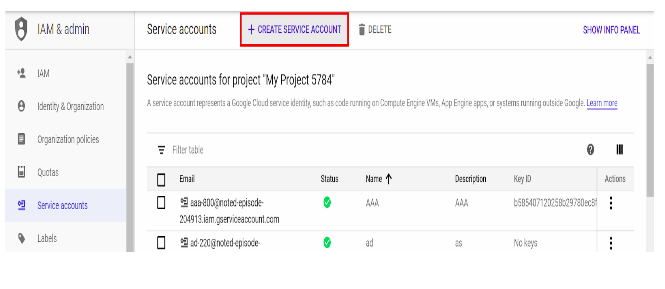
- Click on + Create Service Account.

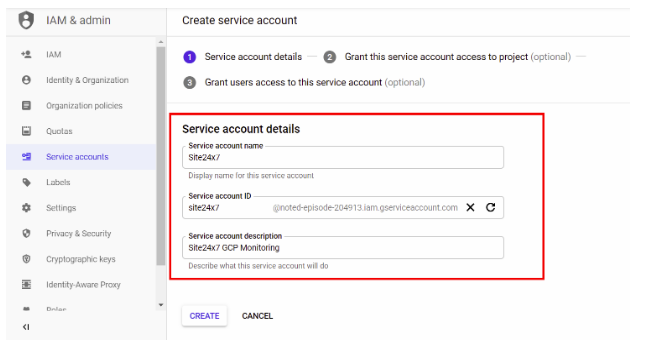
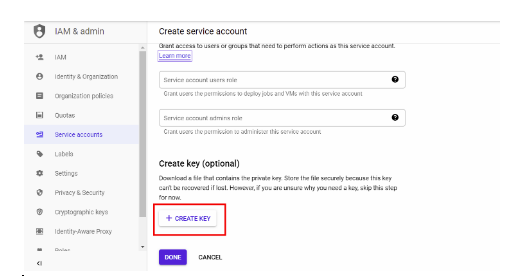
- Provide Service Account Details including the account Name, ID, and Description. Click Create.

- Provide the role Viewer for the project.


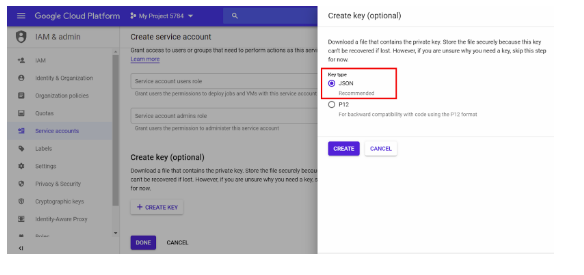
- Click on + Create Key.

- Select the Key Type as JSON and click Create.

There are two types of service account keys
GCP-Managed keys:
These keys are utilized by Cloud Platform resources, for example, App Engine and Compute Engine. They can’t be downloaded, and are consequently pivoted and utilized for getting paperwork done for a limit of about fourteen days. The turn procedure is irregular and random; use of the new key will bit by bit increase and down over the key’s lifetime. We prescribe reserving the open key set for a service account over a time period of 24 hours, so that you always have access to approach the present key set.
Client managed keys:
These keys are made, downloadable, and oversaw by clients. They terminate 10 years from creation, and stop confirming effectively when they are erased from the service account.
Usage of a Service account
There are three different ways to use service accounts to get access to Google APIs:
- Validation utilizing RSA private keys
- Approval utilizing Cloud IAM strategies
- Through deploying jobs on Google Cloud Services
Validation utilizing RSA private keys:
All service accounts have Google Cloud-managed key sets which are routinely pivoted, and the private keys cannot be accessed directly.
It’s likely possible to manually make a user managed key pair. Google Cloud will create the private/public keys, where it stores the public key, and gives the private key to the client. The key pair will be not able to validate to Google when the key pair is erased from the Service account.
Approval utilizing Cloud IAM arrangements:
All service accounts have Cloud IAM approaches that award access to the Service account. A few authorizations permit clients to imitate, or become, the Service account dependent on the user’s accreditations.
Through deploying jobs on Google Cloud Services:
Some Google Cloud Services, for example, Compute Engine, App Engine, or Cloud Functions, permit you to run a job, (for example, a VM or a Function) that runs as the identity of a Service account.
To deploy jobs in this way, Service account must be conceded any essential authorizations for the ideal service, and the user account should likewise be granted with the permissions on the Service account. It is more likely that the Google Cloud Service keeps up Cloud IAM permissions on the Service account, although it is performed automatically.
Understanding of Service Account keys
A user or service has a provision for generating external keys (RSA) which are used to authenticate directly to google cloud as a service account. Further these are used with applications default credentials or with gcloud auth commands. Any user who has got access to these key materials can now have full access to resources for which service account is linked to. These private keys have the highest concern, so they are prone to be less secure. This makes rotating key material insecure.
Thus these advantages of service account makes it a biggest asset on GCP to authenticate the data from Google API’s. It also adds more simplicity and security to its services.