Cloud VPC Firewall Management With Service Accounts
Cloud VPC Firewall Management With Service Accounts
Google Cloud Platform firewall rules lets us allow or deny traffic to and from your virtual machine instances based on a configuration you specify. Enabled GCP firewall rules are always enforced, protecting your instances regardless of their configuration and operating system, even if they have not started up.
Every VPC network function has a distributed firewall. The firewall rules are defined at the network level, connections are allowed or denied on a per-instance basis. You can think of the GCP firewall rules as existing not only between your instances and other networks but between individual instances within the same network.
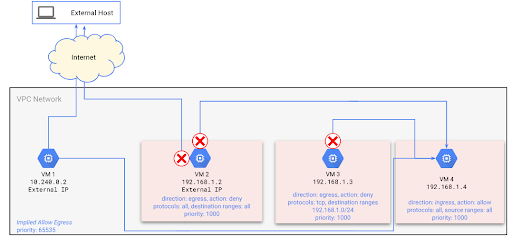

Firewalls provide the network defense for any infrastructure. Google Cloud VPC firewalls provide that controlling network access to and between all the instances in your VPC. Firewall rules determine who is allowed to talk to whom and more importantly who can not. Configuring and managing IP-based firewall rules is a complex and manual process that can lead to unauthorized access if done incorrectly.
While running a complex application in a production environment, you must be familiar with service accounts in Cloud Identity and Access Management that provide an identity to applications running on virtual machine instances. The simplification of application management lifecycle by providing mechanisms to manage authentication and authorization of applications provided by service account. They provide a flexible and secure mechanism to group virtual machine instances with similar applications and functions with a common identity. Security and access control is provided at the service account level.
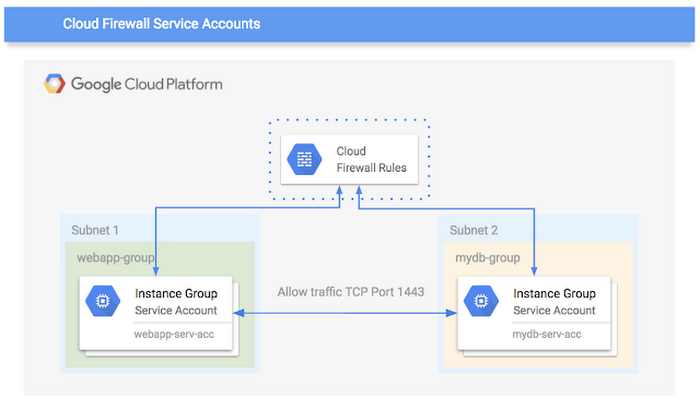

when migrating any application to cloud it scales up or down, new VMs are automatically created from an instance template and assigned the correct service account identity. when the VM starts up, it gets the right set of permissions and within the relevant subnet, so firewall rules are automatically configured and applied by using service accounts.
The combination of Cloud IAM ACLs with service accounts allows application managers to express their firewall rules in the form of intent. for example, allowing access to “Service-Accounts-demo” servers to access “Demo-database”. Therefore no need to manually manage Server IP Address lists which simultaneously reduces human error.
This process is more manageable than maintaining IP address-based firewall rules, which can neither be automated nor templated for transient VMs.


