Understanding of all the GCP service accounts with the help of use cases
Understanding of all the GCP service accounts with the help of use cases
10 December 2021
Google Cloud Platform (GCP) is a suite of public cloud computer services used by Google. This system includes a vast array of organized solutions for compute, storage space and also application development that work on Google hardware. Building applications on GCP needs the concept of a service account, an unique Google account that belongs to the application or a digital device which can be treated as an identification in addition to a source. Depending on the use instance, there are different techniques to manage solution accounts and also to provide accessibility to resources.
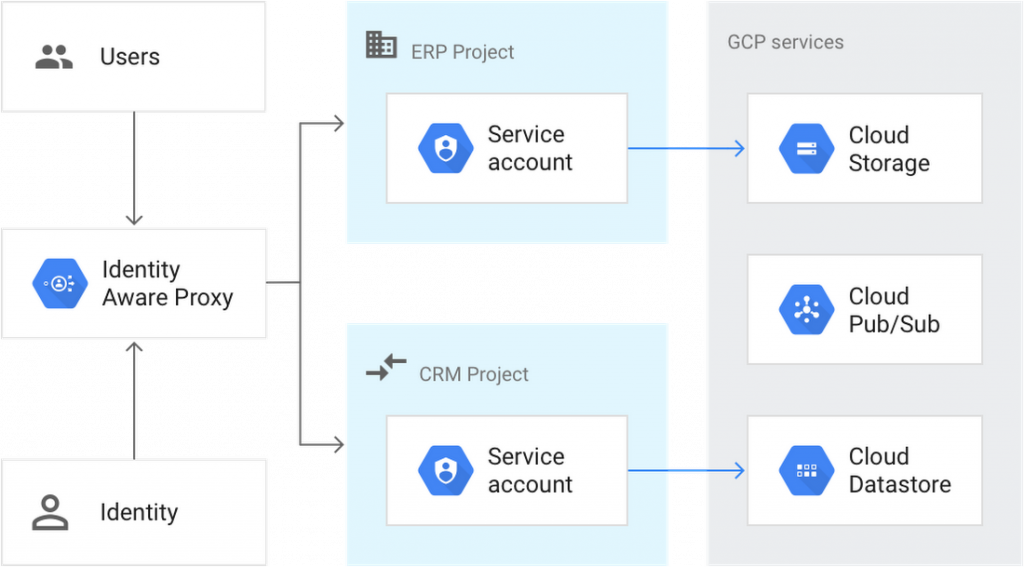
Use instance 1: Internet application accessing GCP sources.
Identity-Aware Proxy (IAP) is a GCP service that intercepts internet demands sent out to the application, verifies the user making the request using the Google Identification Service, and also just allows the requests if they originate from a user we authorize.
Imagine the individuals are working into an internet app for which they are licensed via Cloud Identity-Aware Proxy (IAP) and also do not call for straight access to the underlying GCP resources– just to the web application that utilizes the GCP resources. So the internet application makes use of a service account to grant permission to accessibility GCP services, as an example, Datastore. For this case the service account has a ratio 1:1 map to the internet app which is the identity of the web application. To begin with, first you make the service account in the GCP job that gives the web application, and you give the permissions to your app which needs to access GCP sources to the solution account. Lastly, configuration your application to make use of the solution account qualifications.
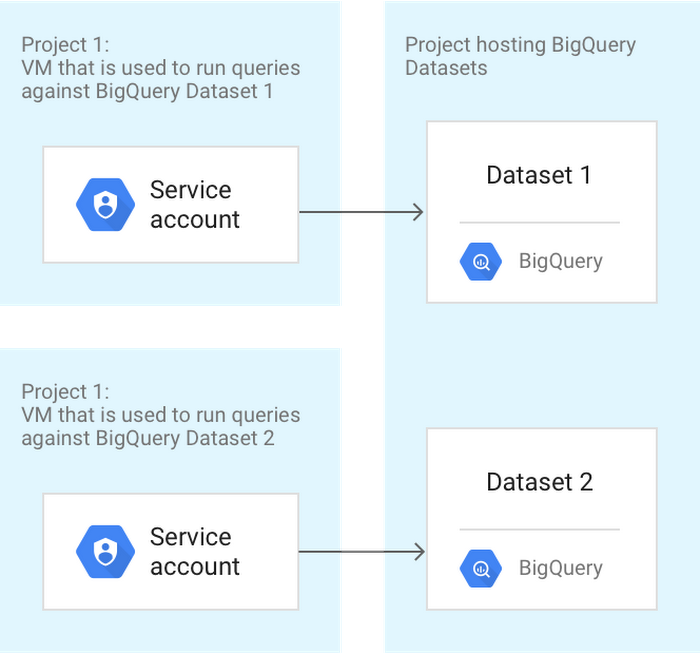
Usage case 2: Cross-charging BigQuery use to various cost facilities
BigQuery is a fully-managed, web server much less data storage facility that allows scalable evaluation over pet bytes of information. It is a Platform as a Service (PaaS) that supports querying using ANSI SQL. It also has built-in device finding out capacities
In this format, department users examine a common BigQuery dataset using a customized application so that the inquiries must be cross-charged to the individuals’ expense facility. The application works with a VM with a solution account that has the proper authorizations to make queries in opposition to the BigQuery dataset.
Every division has a series of projects which are identified such that the sources used in that project emerge in the billing exports. Each department additionally had to run the application from their designated project so that the queries run against BigQuery can be properly cross-charged.
To form this for every of the departments’ projects, in each of the projects executing the queries, appoint the IAM approvals needed to run queries against the BigQuery datasets to the application’s service account.
IAM allows you to approve granular access to detailed Google Cloud resources and helps prevent access to various other sources. IAM allows you to adopt the safety and security principle of least privilege, which states that no one ought to have a lot more approvals than they really need.
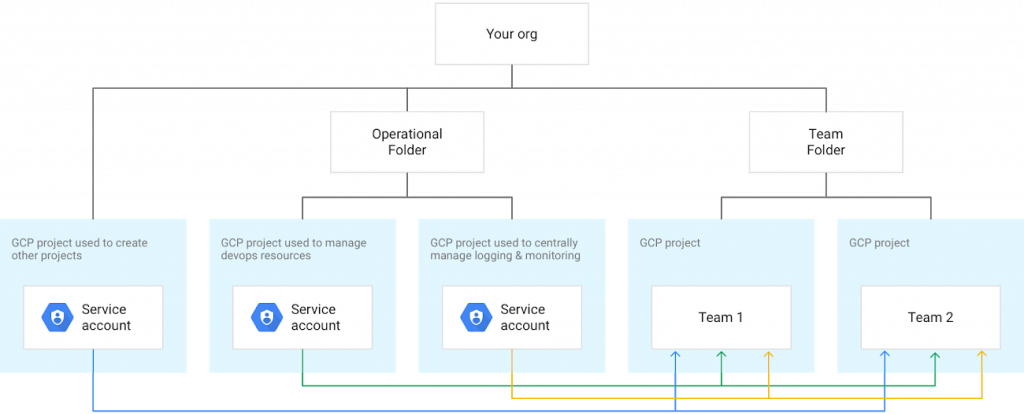
Usage case 3: Managing service accounts used for operational as well as admin tasks
As a system controller or operator in charge of managing a GCP environment, you want to centrally run typical procedures such as provisioning environments, bookkeeping, etc., throughout your GCP atmosphere. In this circumstances, you’ll need to create a diversity of service accounts with the ideal authorizations to permit numerous jobs. These service accounts are most likely to have upraised advantages and have actually been sanctioned given at the ideal level in the hierarchy. And also like for all service accounts, you need them to adhere to best procedures to stop them from being exposed to unapproved users. For example, you must include a job line to the projects where these operational service accounts are produced to help prevent them from being accidentally deleted.
Crazy for solution accounts
As you can see from the usage instances discussed over, one version does not fit all as well as you will require to take on the proper operational model to fit your use situation. We hope walking through these use instances aids you to think of where you rationally should place your service accounts. To get more information regarding service accounts, try among the following tutorials to see just how to use service account credentials with the GCP calculate service of your choice:
– Making use of service accounts with GKE to confirm to GCP
– Making use of service accounts with Compute engine instances to validate GCP
– Service account for AppEngine