What is an RSA algorithm?
What is an RSA algorithm?
Introduction
RSA algorithm is a public key encryption technique, used to securely transmit messages over the internet. It is considered as the most secure way of encryption. In this cryptography method, both the public and the private keys can encrypt a message; the opposite key from the one used to encrypt a message is used to decrypt it.
This algorithm was invented by Rivest, Shamir and Adleman in 1978 and hence it’s named as the RSA algorithm.
The History of Cryptography
Cryptography is the technique for securing the communications between two parties made in the presence of any third party. There are multiple algorithms present for this. RSA algorithm is one of them.
Throughout history, people have needed to protect their secrets. For thousands of years, people have been using codes and ciphers to protect those secrets. Earlier, cryptography was treated off as an art; it was only studied by writers and artists. It was used as early as 1900 BCE in Ancient Egypt. During these times the Egyptians would create a code using hieroglyphics by switching the order of them and only people who knew the order could translate the message
How it works?
If you had a chance to share the code with your friend beforehand, then either of you can send an encrypted message at any time, knowing that you two are the only ones with the authority to read the message contents. But what if you didn’t have a chance to share the code beforehand?
This is one of the fundamental problems of cryptography, which has been addressed by public-key encryption schemes like RSA.
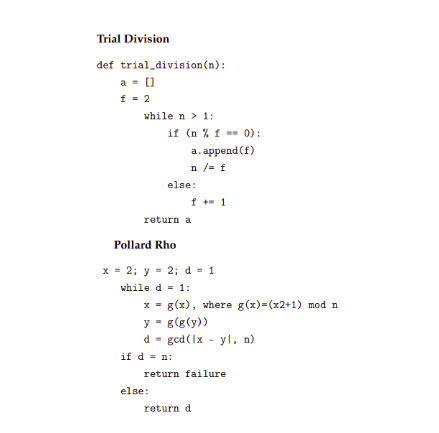
There are multiple algorithms that are used along with the RSA algorithms. These are following:
- Pollard Rho
- Trial Division
- Continued Fraction Factoring
- Quadratic Sieve etc.
Pseudo-code of the Algorithms

Where RSA algorithms can be used?
RSA encryption method is mostly used in combination with other encryption schemes, or for digital signatures. This method can prove the authenticity and integrity of a message. We cannot use it to encrypt entire messages or files, because it is less efficient. Also, it’s more resource-heavy than symmetric-key encryption.
This encryption technique is mostly used in web browsers, chat applications, email, VPNs, and any other types of communications which require people you haven’t met before or if we are securely sending data to servers.
Conclusion
The RSA is considered safe to use. The criteria for this is: “it needs to be implemented correctly and use a key that falls within the correct parameters”. There are very few chances of security threat, if we use keys of larger bits like 4096 bits or more.