What is a Bastion Host?
What is a Bastion Host?
A bastion host is a special purpose computer on a network that is deliberately exposed to a public network and configured to withstand attacks. From a secured network perspective, it is the only node exposed to the outside world and is thus very prone to attack. Usually a single application is hosted by the computer, for example, a proxy server, and all other services are removed or limited to reduce the threat to the computer.
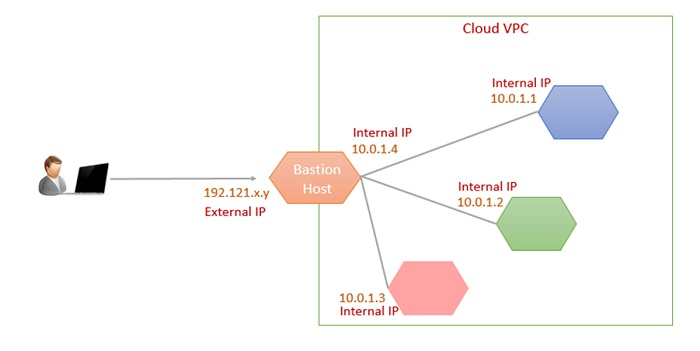

What is the purpose of a bastion host?
By using a bastion host, you can connect to instances that do not have an external IP address associated with it. This approach enables you to connect to a development environment or for the management of the database instance for your external application, for example, without configuring additional firewall rules.
Domain name system, Web and File Transfer Protocol (FTP) servers. Firewalls and routers can also become bastion hosts are the common uses of Bastion Host.
Additionally, the best practice for an infrastructure administration is to limit access to the resources. This is where Bastion Host comes into the play, by allowing only itself to be communicated to the public network and restricting the public access to all the other resources which are in the same VPC (Virtual Private Cloud) network. Bastion Host connects to all the other resources via internal IP address as a perk of residing into the same VPC network along with other resources which can be a database, a firewall or another private server instances.
Creating a Bastion Host configuration
You can connect to an instance that does not have an external IP address with the help of Bastion host. This approach enables you to connect to a development environment or manage the database instance for your external application, for example, without configuring additional firewall rules.
Launch a sample webserver instance
Execute gcloud command to launch a private instance from the cloud shell and append –no-address to restrict the public access to this instance
gcloud compute instances create webserver --zone=us-central1-a --machine-type=f1-micro --no-address --image-family=debian-9-stretch-v20190326 --image-project=debian-cloud --boot-disk-size=10GB --boot-disk-type=pd-standard --boot-disk-device-name=webserver
Create a Bastion Host
Execute gcloud command to launch Bastion Host instance from the cloud shell
gcloud compute instances create bastion --zone=us-east1-b --machine-type=f1-micro --tags=bastion --image-family=debian-9-stretch-v20190326 --image-project=debian-cloud --boot-disk-size=10GB --boot-disk-type=pd-standard --boot-disk-device-name=bastion
Restrict firewall rule settings for SSH
The default setting for default or auto-type network is to allow SSH access from any source IP address. Create a new firewall to restrict access to just your source IP address.
gcloud compute firewall-rules create bastion-ssh --direction=INGRESS --priority=1000 --network=data --action=ALLOW --rules=tcp:22 --source-ranges=[YOUR IP HERE]/32 --target-tags=bastion
Create a Firewall rule to allow traffic from the bastion to all other instances
gcloud compute --project=myproject firewall-rules create bastion-fwd --direction=INGRESS --priority=1000 --network=data --action=ALLOW --rules=all --source-tags=bastion
Connect to the Bastion Host via SSH and verify access to webserver
In order to connect to the webserver instance, SSH into the bastion instance and then execute the command “ssh -a webserver”, on executing this command you will be able to connect to webserver instance even though the external IP of the instance is not reachable .


