Configuring Okta as IdP with Spring Security using SAML
Configuring Okta as IdP with Spring Security using SAML
16 February 2022
This blog is about how to build a Spring Boot application that leverages Okta’s Platform API for authentication via SAML. SAML (Security Assertion Markup Language) is an XML-based standard protocol for securely exchanging authentication and authorization information between entities—specifically between identity providers, service providers, and users. Well-known IdPs that are used world wide include Salesforce, Okta, OneLogin, and Shibboleth.
Sign Up for an Okta Developer Account
To start developing with the Okta integration, I have created a new developer account at
https://developer.okta.com. Make sure you take a screenshot of your unique URL or write down your Okta URL after you’ve signed up. You’ll need this URL to get back to the Okta user interface to log in into your Okta developer account.
You’ll receive an email to activate your developer account and change the temporary password by clicking on the link in the email. After completing these steps from your email, you’ll land on your dashboard with some annotations about “apps” to guide you about the Okta dashboard.
Create a SAML Application on Okta
If you’re new to both Spring Boot and Okta, this blog might work better for you.
The first thing you’ll need to do is create an Okta developer account at okta.com/integrate/signup.
NOTE: This is a different signup URL than our normal developer integration flow, and is specifically for folks building integrations with Okta.
After activating your account, log in to the account.
Click Add Applications in the top right of the Dashboard to continue. This will bring you to a screen with a Create New App green button on the left of the screen.
Click the button and choose SAML 2.0 for the sign on method. Click the Next button at the left bottom of the screen.
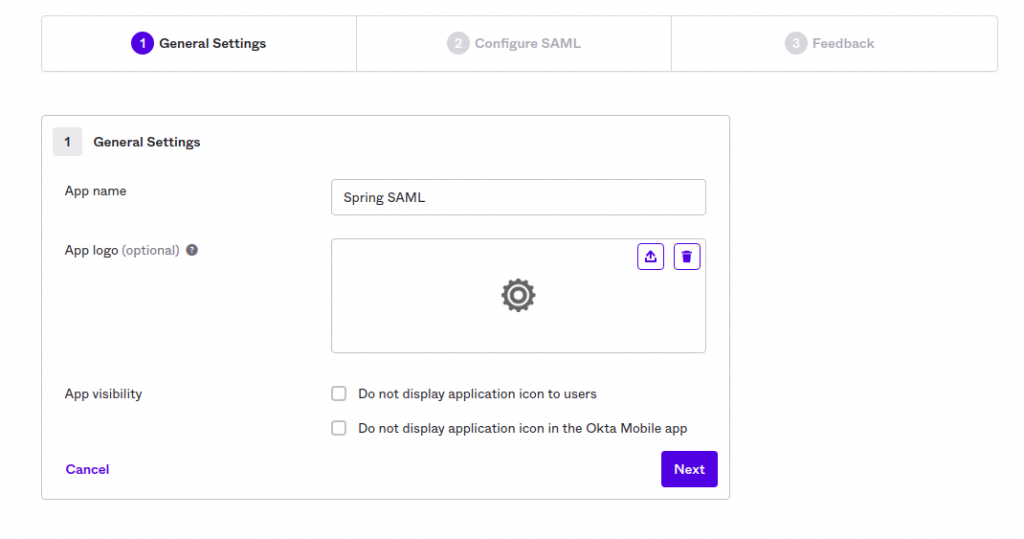
The next screen will take you to the General configuration page. I used “Spring SAML” as my app name, but any name will work as per your interest.

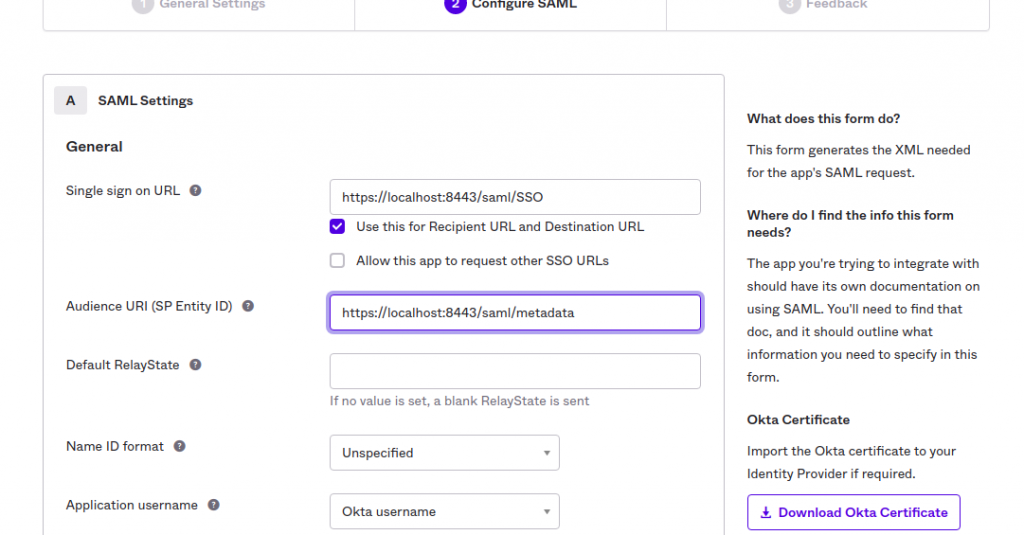
Click the Next button. This brings you to the second step, configuring the SAML screen. Enter the following values:
- Single sign on URL: http://localhost:8443/saml/SSO
- Audience URI: http://localhost:8443/saml/metadata

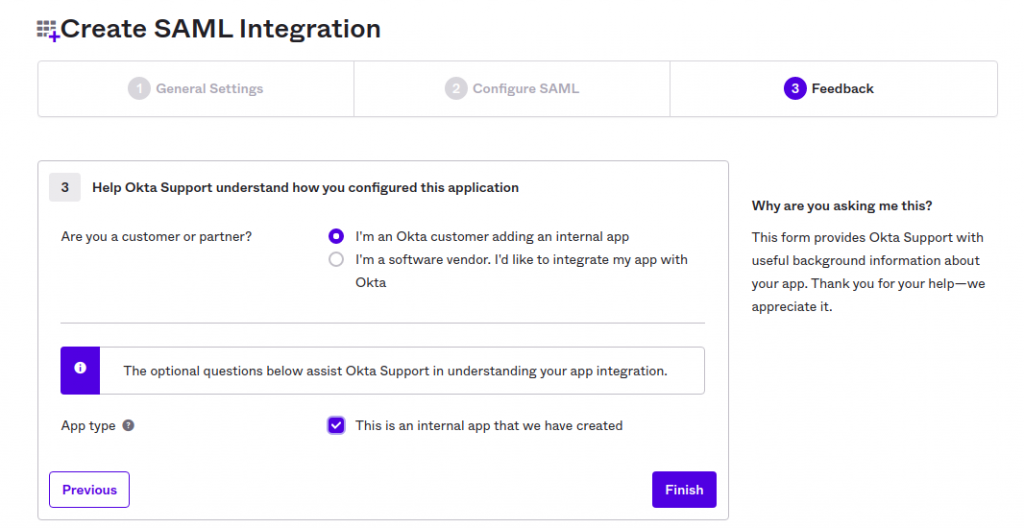
Scroll to the bottom of the form and click Next to continue to the next screen. This will bring you to the third and final step, feedback. Choose “I’m an Okta customer adding an internal app” and optionally select the checkbox of the App type.

Click the Finish button at the bottom of the screen to continue to add the App. This will bring you to the application’s “Sign On” tab which has a section with a link to the metadata of your application in a yellow box shown in the below-attached screenshot. Copy the Identity Provider metadata link from the yellow box as you’ll need it during the configuration of your Spring Boot application.

The final and last setup step you’ll need is to assign people to the application that you created. Click on the Assignments screen/tab and the Assign > Assign to People button to add the users. You’ll see a list of people with your account in it in the assignees list.

Create a Spring Boot Application with SAML Support
Go to this link https://start.spring.io in your favorite browser and select Security, Web, Thymeleaf, and DevTools as dependencies while creating a Spring Application.
Add the spring-security-saml-dsl dependency to your pom.xml of the project.
<dependency> <groupId>org.springframework.security.extensions</groupId> <artifactId>spring-security-saml-dsl</artifactId> <version>1.0.0.M3</version> </dependency>
In src/main/resources/application.properties, add the following key/value pairs in the application.properties file. Make sure to use the “Identity Provider metadata” value from the Okta (hint: you can find it under the “Sign On” tab in your Okta application).
server.port = 8443 server.ssl.enabled = true server.ssl.key-alias = spring server.ssl.key-store = classpath:saml/keystore.jks server.ssl.key-store-password = secret security.saml2.metadata-url = <your metadata url>
From the terminal, navigate to the src/main/resources directory of the application and create a saml directory. Navigate into the saml directory and run the below command. Use “secret” as a password when prompted for a Keystore password.
keytool -genkey -v -keystore keystore.jks -alias spring -keyalg RSA -keysize 2048 -validity
Create a SecurityConfiguration.java file.
import static org.springframework.security.extensions.saml2.config.SAMLConfigurer.saml;
import org.springframework.beans.factory.annotation.Value;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.method.configuration.EnableGlobalMethodSecurity;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
@EnableWebSecurity
@Configuration
@EnableGlobalMethodSecurity(securedEnabled = true)
public class SecurityConfiguration extends WebSecurityConfigurerAdapter {
@Value("${security.saml2.metadata-url}")
String metadataUrl;
@Value("${server.ssl.key-alias}")
String keyAlias;
@Value("${server.ssl.key-store-password}")
String password;
@Value("${server.port}")
String port;
@Value("${server.ssl.key-store}")
String keyStoreFilePath;
@Override
protected void configure(final HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/saml*").permitAll()
.anyRequest().authenticated()
.and()
.apply(saml())
.serviceProvider()
.keyStore()
.storeFilePath(this.keyStoreFilePath)
.password(this.password)
.keyname(this.keyAlias)
.keyPassword(this.password)
.and()
.protocol("https")
.hostname(String.format("%s:%s", "localhost", this.port))
.basePath("/")
.and()
.identityProvider()
.metadataFilePath(this.metadataUrl);
}
}
Create an IndexController.java file in the same directory/saml directory and use it to set the default view to the index that needs to be displayed.
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.RequestMapping;
@Controller
public class IndexController {
@RequestMapping("/")
public String index() {
return "index";
}
}
Since you chose Thymeleaf dependency when creating your application, you can create a src/main/resources/templates/index.html file and it will automatically be rendered after you sign-in to the login page. Create this file and populate it with the following basic HTML code.
<!DOCTYPE html> <html> <head> <title>Spring Security SAML Example</title> </head> <body> Hello SAML! </body> </html>
Run the App and Login with Okta
Start the app using your IDE like IntelliJ/Eclipse/VScode or mvn spring-boot:run and navigate to https://localhost:8443
Enter the login credentials in the login page. Once successfully logged in you should be able to see “Hello SAML”.