09 October 2020
Let’s start with the introduction of gRPC, Enclave, Asylo…
gRPC
You must have heard about Remote Procedure Call (RPC). It is a request-response protocol.
gRPC is a one kind of RPC which is a free and open-source framework developed by Google. It allows you to define Request and Response for RPC (Remote Procedure Call).
gRPC server is modern, fast and efficient, built on top of HTTP/2, low latency, supports streaming, language-independent and makes authentication, load balancing, logging and monitoring super easy to plug into.
An enclave
On traditional systems, the Operating System (OS) kernel has unlimited access to a machine’s hardware resources. OS kernel exposes most of its access permissions to a root user without any restrictions. As a result, if the hacker can execute code with root privileges, they can compromise every secret and bypass every security policy on the machine. For example, if the hacker obtaining root access on a machine that manages TLS keys, those keys may be compromised.
Enclaves are an emerging technology that changes this equation. An enclave is a special execution context in which code can run shielded from even the OS kernel, with the assurance that even a root privileged user can not extract the secrets of the enclave or undermine its integrity. This security is allowed by hardware-isolation technologies such as Intel SGX or ARM TrustZone, or even by additional software layers such as a hypervisor.
Asylo
Asylo is an open source platform for developing enclave applications. It specifies an abstract model of the enclave that can be transparently mapped onto a variety of enclave technologies (i.e., enclave backends). Asylo provides a platform for software development that serves a growing variety of use cases. In a way, the backend of the enclave can be seen as a special purpose built-in computer running inside a traditional machine, with Asylo providing the necessary runtime for that embedded computer.

Running gRPC Server Inside an Enclave
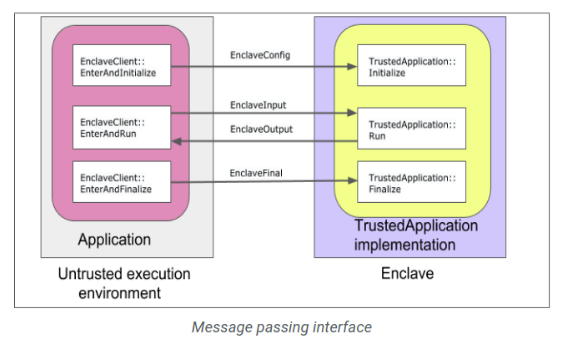
Let’s start our main objective of this blog i.e. running gRPC server inside an Enclave. This section explains how to run a gRPC server within an enclave and how to communicate with it from a client running in an untrusted environment.
The runtime of the Asylo enclave features rich POSIX support which allows full-featured gRPC servers to run within an enclave. Enclaves can then act as secure nodes in your cloud and distributed network.
You can use the Asylo Docker image and run the bazel commands below inside an interactive Docker terminal.
Defining the gRPC service:
Lets implement a simple translation service inside an enclave.
This is a simple example for request and response of a word to be translated.

Setting up a server enclave:
To set up the server, the enclave must know the desired server address and the server must wait for the appropriate amount of time before shutting down the server. You can pass this information through the Initialize method which accepts an EnclaveConfig.
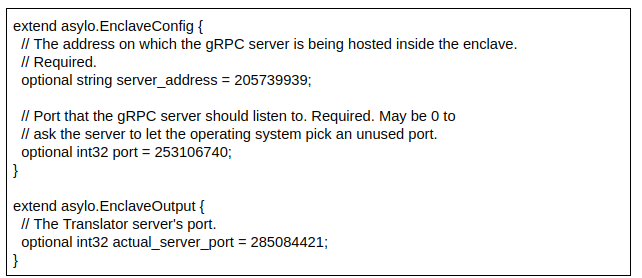
This example maps the logic of configuring gRPC server to TrustedApplication’s virtual methods as follows:
- The Initialize method constructs and launches the server using the information from the EnclaveConfig.
- The Run method writes the server’s final port to an EnclaveOutput message extension, and returns an OK status. All our interaction with the enclave goes through gRPC, so Run doesn’t need to do any other work.
- And the Finalize method shuts down the gRPC server.
Initializing the server:
To configure and start the server the Initialize method uses grpc::ServerBuilder. The server setup requires the server_address extension from the EnclaveConfig and the service member described above. The Initialize process logic ensures the server is initialized and started just once.
If the EnclaveConfig does not have an extension to server_address, or if the server does not start, then Initialize returns a non-OK status. Else, Initialize returns an OK Status:

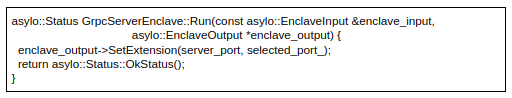
Running the server:
The Run method returns an OK status and an EnclaveOutput containing the gRPC server allocated port:
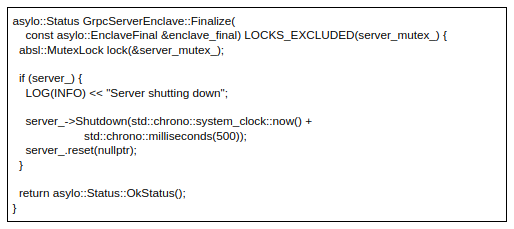
Finalizing the server:
The Finalize approach shuts down the server for all remaining RPCs, with a 500 millisecond timeout. Finalize also tells the user that it is shutting down the server: