Introduction to Cloud Identity
Introduction to Cloud Identity
06 August 2021
What is Cloud Identity?
Cloud Identity is a cloud based Identity-as-a-Service and mobile device management solution for deciding who has appropriate access to an organization’s cloud resources and services.
When we refer to Identity-as-a-Service we talk about identity and access management, sometimes referred to as IAM. As organizations are adding more cloud services, applications, devices and tool sets to their domains, the process for managing users across projects and their authorization becomes more complex. Cloud Identity will allow us to centrally manage our contributors access to the platform, and ensure that our project business data is secure. Organizations can use Identity-as-a-Service solutions to manage user identities and access permissions across their entire domain to enforce security policies and roles. Users can access all enterprise cloud applications by signing in one time for all services through a process called Single Sign-On. Also, these organizational data and devices can be protected by an extra layer of security known as 2-Step Verification, also known as Multi-Factor Authentication. As an admin, using Cloud Identity unlocks advanced Google Cloud security features so we can grant permissions to users’ roles across the organization’s domain based on their needs and tasks
To get started with Cloud Identity, we will need a registered domain. A domain is the unique name that appears after the sign in email addresses and after www in web addresses. Domains typically take the form of any organization’s name and a standard internet suffix such as, yourbusiness.com or stateuniversity.edu. It is the address on the internet which allows people and services to directly communicate and work with us or any organization.
Adding Users
In order to add, users need access to organization’s cloud services through Google Cloud Identity, they will need to establish Google Accounts. An account provides a user with a name, a password for signing into cloud services. Each user we add requires a user license.
The deployment of a Cloud Identity domain will often be done in phases. In each deployment phase, we add different types of users based on their particular focus and unique needs. If any of the organization has a large, pre-established directory, Google Cloud Directory Sync (GCDS) is a secure tool that google provides that can help sync users into Cloud Identity domain. GCDS allows us to synchronize our user data in our Cloud Identity domain with our Microsoft Active Directory or LDAP server. GCDS will ensure that Google users, groups, and shared contacts are synchronized to match the information in our LDAP server. The data will never be modified nor compromised. The Lightweight Directory Access Protocol, or LDAP, is an application protocol for querying and modifying directory services running over IP.
Introduction to Security
This module will help us through some of the security features that are available as the Cloud Identity admin. Google takes security, and privacy seriously, and offers tools that help organizations protect their user accounts with a robust combination of technologies that balance security, and end-user convenience. As an admin we can view, and manage the security settings for our users in the Admin console to reinforce, and monitor the security of our Google accounts in several ways. The best practices are viewing users’ security settings, examining the users password strength, and ensuring that they have two-step verification set up, also known as multi-factor authentication, and viewing users behavior reports.


From the admin console we can enforce two-step verification, and ensure password strength. Also if a user loses a device, we can revoke any application specific passwords to ensure that no one can access their account information from that device. Another option is disabling client logins. As an admin, we will be able to turn off access to those less secure applications, further securing our domain. Another security best practice recommendation is to check the user’s account activity report page. Here we can view users’ account status, and activity. This page gives access to all the data from user accounts, and admin statuses, to two-step verification enrollment reports. Along with being able to view users’ activity, we will be able to see which applications are getting access to organization’s business data. With SSO (single sign-on), users can access many applications without having to enter usernames, and passwords in each of them. It works by using SAML (Security Assertion Markup Language). SAML allows secure Web domains to exchange user authentication. For example, an online service provider like Slack or Salesforce, can contact an online identity provider like Google, or another identity service provider to authenticate users who are trying to access secure content. Using SAML, users can use their cloud identity credentials to sign into a pre-integrated list of SSO applications, and also custom Web applications. Cloud identities are able to work with any application that supports the SAML standard.
Introduction to Enhanced Desktop Security for Windows
Enhanced desktop security for Windows allows users to sign into their Windows devices using their Google credentials. It also offers a comprehensive set of device management options which allow, as the Cloud Identity administrator, to manage all devices, desktop and mobile from the admin console. Enhanced desktop security for Windows offers administrators an easy way to manage their Windows device inventory from within G Suite or Cloud Identity. This solution includes two key components, Google Credential Provider for Windows (GCPW) and Windows management.


GCPW also provides the following benefits of additional security such as users get all the security benefits of their Google Account on their Windows 10 device. These features include anti-hijacking features such as 2-step verification and login challenges, SSO experience, Password synchronization, Admin actions such as viewing device details and signing users out of their Google account.
Introduction to Managing Domains
Users can have an identity at one or more of your domains and share the same Google services, and we can manage all this from our admin console. So to add multiple domains to any organization’s Google account we need to sign up for a Cloud Identity domain, and provide a domain name that becomes the primary domain associated with Google account. After that, we can add other domains using the admin console. We can add up to 600 domains to the organization’s Google account. Domains can be added as either a separate domain or domain alias. Domain aliases allow users to send mail with an email address at another domain. For example, users might have two different products each with their own domain. Having aliases for these domains will allow people to send mail using an address from either domain. Users will still receive email though, from their primary domain email. Additionally, we can use multiple domains with single sign on. As long as the SSO system is configured to identify the user by email address, it’ll work smoothly for Google accounts with multiple domains. When we add a domain to our managed Google account, we need to keep in mind some limitations that ensure that we have set up our domains correctly.
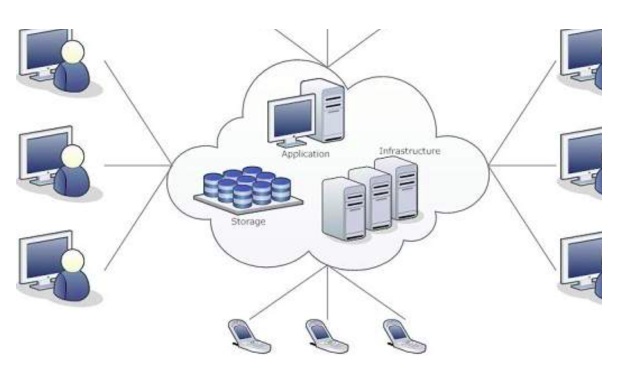

Conclusion
In this blog we got to know about cloud identity, and why having a cloud-based identity as a service solution is beneficial to an organization. Cloud Identity allows us to not only create and manage our users, but it has a robust set of security features that will help keep organization’s data safe. We also got to know about domains, which allows people and services to directly communicate and work with us and an organization. As a result we can use the domain along with Cloud Identity to design and implement organization’s identity and access management approach. Managing users is one of the most important tasks associated with being an identity and access management admin.


