HIPAA Compliance in AWS
HIPAA Compliance in AWS
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is legislation that is designed for US workers to retain health insurance coverage when they change or lose their jobs. It is the standard for protecting sensitive patient data. Any company which is dealing with protected health information (PHI) must ensure that all the required physical, network, and process security measures are in place and followed.
With increasing the use of electronic medical records, HIPAA compliance protects the security and privacy of protected health information (PHI). PHI has a very wide set of personal health-related data, including insurance and billing information, diagnosis data, clinical care data, and lab results such as images and test results.
HIPAA compliance covers the entities, who provide treatment, payment, and operations in healthcare, and business associates (BA), anyone with access to patient information and provides support in treatment, payment or operations. It also includes subcontractors and business associates that deal with patient data. When AWS is dealing with the protected health Information (PHI), customers using AWS services have to follow the rules and regulations of HIPAA compliance.
The HIPAA Privacy Rule deals with the accessing and sharing of medical and personal information of any individual, while the HIPAA Security Rule more specifically deals with national security standards for protecting health data created, received, maintained or transmitted electronically, also known as electronic protected health information (ePHI).
Business Associate Addendum (BAA)
The Cloud service providers such as AWS are considered business associates as per the HIPAA regulations. The Business Associate Addendum (BAA) is an AWS contract under HIPAA rules to ensure that AWS appropriately safeguards protected health information (PHI). It also serves to clarify and limit, as appropriate, the permissible uses and disclosures of PHI by AWS. AWS needs to sign Business Associate Addendum (BAA) before you can start the usage of AWS for your HIPAA compliant workloads.
AWS implements a shared responsibility model where security and compliance is a shared responsibility between AWS and Customer. AWS manages the security of the cloud while security in the cloud is managed by AWS customer.
AWS responsibility for “Security of the Cloud”:
AWS is responsible for protecting the infrastructure which is used by AWS services. AWS manages physical security of the following areas
- Compute
- Storage
- Database
- Networks
- Region
- Availability Zone
- Edge location
Customer responsibility for “Security in the Cloud”:
Customer is responsible security of the Cloud services they select. Customer manages security in the following areas
- Platform
- Operating System
- Applications
- Client side encryption
- Server side encryption
- IAM
- Networking traffic protection
- Customer Data
AWS provides the infrastructure to build your application in HIPAA compliance way. But it is the customer’s responsibility to create cloud infrastructure which ensures confidentiality, the integrity of and security of PHI (Protected Health Information).
HIPAA eligible services in AWS
AWS is HIPAA compliant and can be used to process, store and transmit ePHI. Usage of AWS services doesn’t make it HIPPA compliant directly. There are certain restrictions on used services and requires specific measures to be followed to secure your infrastructure. The list of services applicable for HIPAA compliance is available on HIPAA Eligible Services Reference page. Usage of the services outside this list is not allowed.
Creating HIPAA Compliance Architecture
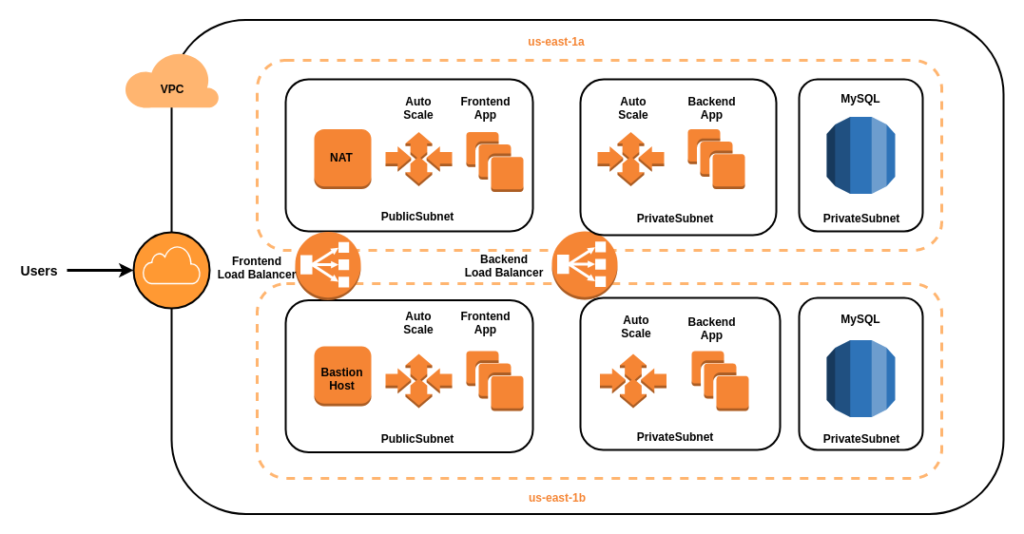

- Create a new VPC with subnets in two different availability zones.
- Create two public subnets in one in each availability zone
- Create four private subnets. Two subnets in each availability zones.
- Create Bastionhost instance in public subnet which allows connection with the instances in private subnet.
- Create NAT instance in public subnet which allows outbound traffic for private instances but prevents inbound traffic.
- Launch frontend instances in public subnets in each availability zone by providing the AMI in the auto scaling group.
- Launch backend instances in private subnets in each availability zone by providing the AMI in the auto scaling group.
- Create two load balancers one for frontend and second for backend
- Integrate the load balancers with corresponding auto scaling groups. It will distribute the traffic between all the instances launched by the auto scaling group. It will also monitor the load on the instances and instruct auto scaling group to launch a new instance if the load is high.
- Launch MySQL instance in multiple availability zones in private subnets
- Create a security group for BastionHost to allow SSH access to it the users of the organizations.
- Allow Bastionhost to access private subnets of backend instances only. Do not allow bastion host to access MYSQL instances.
- Create a security group for backend instances to allow access to the MySQL database.
- (Optional) Create an S3 Bucket if your application needs to store images. Create VPC endpoint between VPC and S3 bucket so that traffic between backend instances and S3 bucket remains private.
- Setup following services outside the VPC (in separate VPC)
- Setup AWS cloud trail for logging and configure it to collect log at S3 bucket which can be used for auditing.
- Used Cloudwatch for monitoring AWS resources.
Encryption and Protection of PHI in AWS
As per the HIPAA compliance guidelines, ePHI should be encrypted in transmission (“in transit”) and in storage (“at rest”).
AWS Security At Rest
AWS Key Management Service (AWS KMS) is a service provided by AWS to manage and control encryption keys. These encryption keys can be used to encrypt data. KMS can integrate with the following AWS services:
- Amazon Elastic Compute Cloud (EC2)
- Amazon Elastic Block Store (Amazon EBS)
- Amazon Simple Storage Service (Amazon S3)
- Amazon RDS (MySQL, PostSQL)
- AWS Directory Services
- Amazon Aurora
- Amazon DynamoDB
- Amazon Redshift
- AWS Snowball
AWS KMS is highly available, durable and scalable service. Therefore AWS KMS is highly recommended for implementation of HIPAA security compliance requirements.
AWS Security In Transit
The connection between Client and web application is going through the load balancers. There are two load balancers, one for frontend and one for the backend. In order to encrypt traffic between client and web application, we have to set up an SSL certificate in the load balancer. We can use AWS Certificate Manager (ACM) to create an SSL certificate. This certificate is deployed to load balancers. We have to create two SSL certificate one for frontend load balancer and second for backend load balancers. Now the communication between frontend and backend is also encrypted. We have to create an SSL certificate for S3 bucket. Then the traffic between the Backend load balancer and S3 bucket will be encrypted.
That was all on the HIPPA Compliance in AWS. For more such interesting articles tune in to our blog posts. Also, we are happy to share that Tudip is recognized as Top Healthcare Software Development Companies on Software Development Company.


